
When a global financial services firm faced growing compliance demands, they needed a scalable, traceable solution to audit their n8n workflows. The problem was universal: 30% of firms have faced fines due to poor record-keeping in the past five years. As 25% of Fortune 500 companies adopt n8n for business-critical workflows, the question shifts from whether to automate to how to automate securely.
Automation without governance creates liability. Enterprises don't reject automation—they reject risk. If your workflows can't prove where data lives, who touched it, and how it's protected, the deal stalls. For regulated industries operating under GDPR, HIPAA, SOC 2, or ISO 27001, comprehensive audit trails transform from nice-to-have features into regulatory requirements.
Traditional workflow automation platforms create a dangerous blind spot. When workflows execute automatically, touching sensitive data across dozens of systems, organizations face three critical gaps:
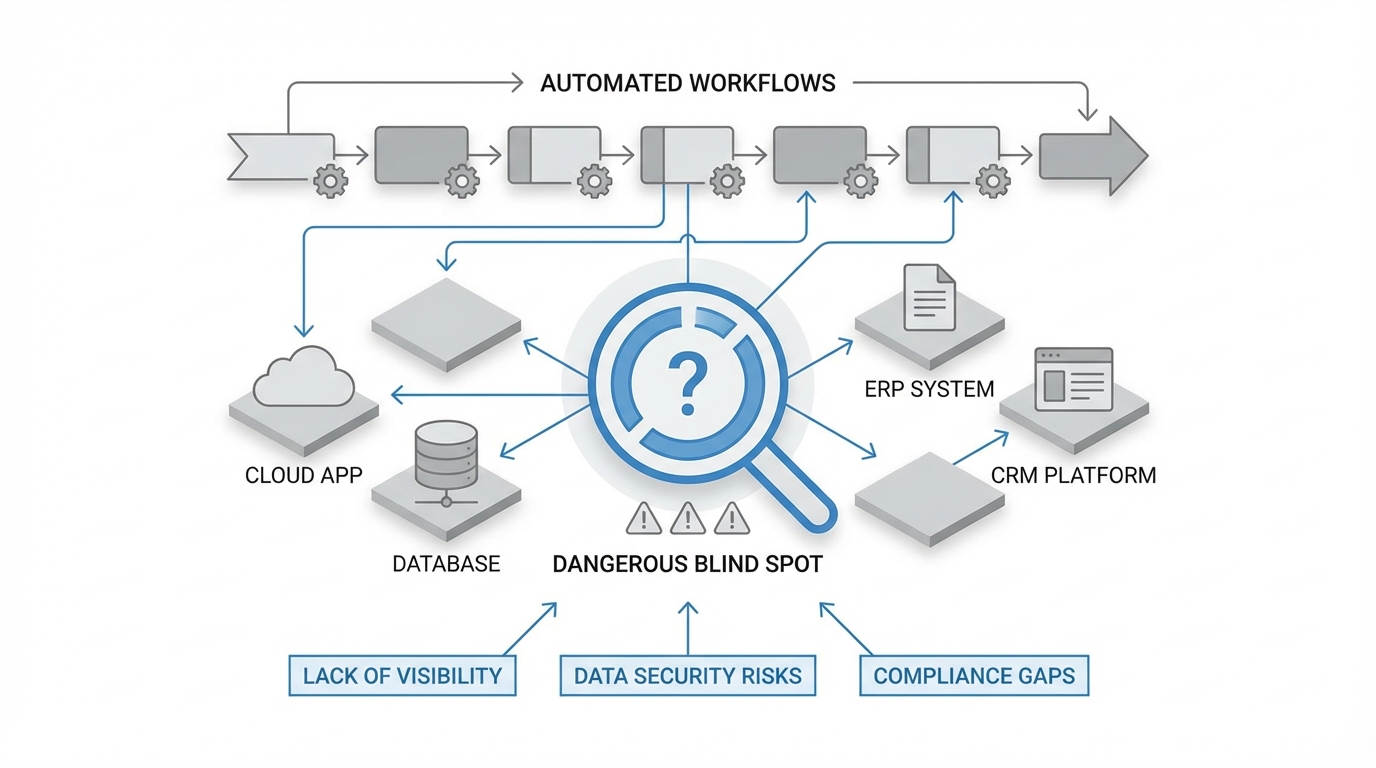
Lack of Traceability
Without detailed logging, teams cannot answer fundamental questions during audits: Who created this workflow? When was it last modified? Which user triggered this execution? What data did it access?
Insufficient Access Controls
Many organizations discover only after a disruption that their automation estate has grown beyond control: workflows are undocumented, access is unrestricted, and critical processes rely on ad hoc scripts with no rollback or monitoring. This creates compliance violations waiting to happen.
Manual Compliance Burden
Auditing workflows manually was time-consuming, error-prone, and failed to meet real-time compliance demands. Finance teams keep spreadsheets tracking workflow changes. Security teams manually review execution logs. Compliance officers spend weeks preparing audit documentation.
The consequences are measurable. When regulators requested evidence during an annual exam, export time fell from days to minutes at a fintech lender with immutable audit trails, saving six figures in potential fines.
Securing n8n workflows for enterprise auditability requires a layered security architecture that addresses authentication, authorization, logging, and data protection.
RBAC is a way of managing access to workflows and credentials based on user roles and projects. You group workflows into projects, and user access depends on the user's project role. This enables separation of duties required by regulatory frameworks.
n8n provides granular role types:
n8n uses projects to group workflows and credentials, and assigns roles to users in each project. This means that a single user can have different roles in different projects, giving them different levels of access. For example, a data engineer might have Editor permissions in the Marketing Analytics project but only Viewer access to Finance Compliance workflows.
Enterprises rarely want standalone login systems. n8n integrates with identity providers (Okta, Azure AD, etc.), enabling Single Sign-On (SSO) and central policy enforcement. SSO, SAML, and LDAP are available with n8n's Enterprise plan, allowing organizations to enforce password policies, session timeouts, and conditional access rules centrally.
n8n should counter weak authentication by enforcing strong passwords with MFA, integrating with OIDC or SAML for centralized access control, applying least-privilege roles, and configuring sessions and API tokens to be short-lived, rotated often, and scoped minimally. This eliminates the risk of credential stuffing attacks and ensures departed employees lose access immediately when disabled in the central identity provider.
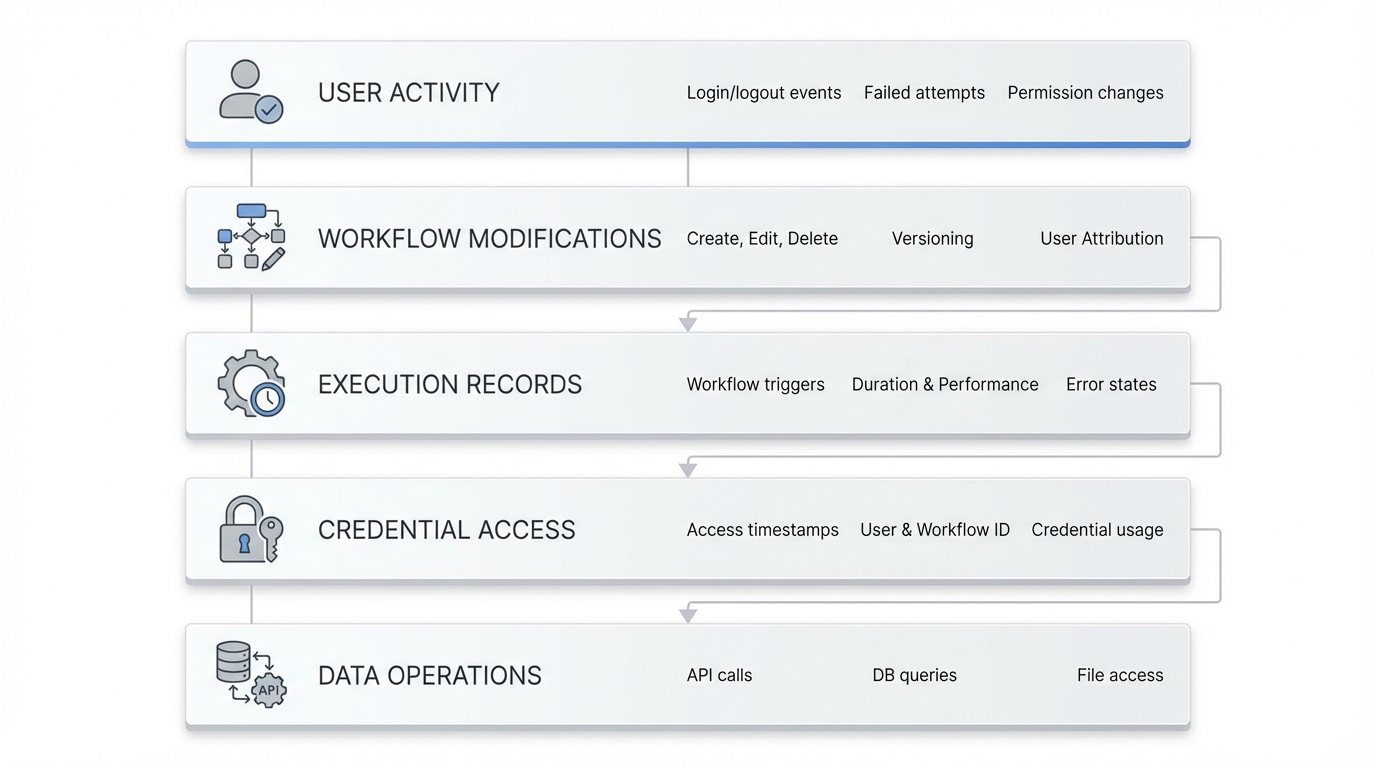
Every workflow edit, execution, and deployment can be logged. This makes compliance audits far easier and gives internal teams confidence that automations can be traced. Authorized users can query the log info as necessary to trace actions to individual users. We keep audit log history and historical activity records for at least 12 months, with at least the last three months immediately available for analysis.
Enterprise audit trails capture:
Write-once storage, cryptographic hashing, and chained log entries ensure that any alteration breaks the chain or hash, flagging tampering attempts. This immutability proves to auditors that logs haven't been retroactively modified to hide security incidents.
The n8n editor should be hidden behind a VPN or allow-listed IPs, with inbound traffic controlled through firewalls or cloud security groups. The admin UI must never be exposed directly to the internet. For high-security environments, consider binding the editor interface to localhost only and exposing it through a bastion host or SSH tunnel.
Production deployments should implement:
Integrate with 3rd-party secret management tools (HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) to securely fetch and inject your encrypted credentials. This prevents storing API keys, database passwords, and service account tokens directly in workflow definitions.
External secret management provides:
Unlike SaaS platforms, n8n can run entirely inside a private cloud or on-premises environment. Sensitive data never leaves your controlled infrastructure—a critical requirement for GDPR, ISO 27001, or SOC 2 compliance.
n8n aligns its security program to SOC 2, a standard framework for security compliance. That means we have implemented processes and follow procedures that uphold high standards of security for our customers' data. We undergo continuous evaluation and annual audits by an independent auditor.
For self-hosted deployments, organizations must implement controls around:
For regulated teams—finance, healthcare, public sector—data location, isolation, and control are non-negotiable. Self-hosting n8n lets you pin data to a specific geography (EU, US, APAC), enforce network boundaries (VPC, private subnets, IP allowlists).
n8n can be configured to support GDPR and similar data protection regulations. Implement data minimization in your workflows, maintain audit logs for data processing activities, and ensure your automation design allows data subject access, correction, or deletion requests.
Patient data must remain fully compliant with HIPAA. Self-hosted n8n provides a clear advantage. Healthcare organizations must implement Business Associate Agreements, encrypt Protected Health Information at rest and in transit, maintain detailed access logs showing who viewed patient data, and implement automatic session timeouts to prevent unauthorized viewing.
Automated alerts on bulk downloads helped detect and stop an insider threat at a hospital chain, avoiding HIPAA breach penalties and reputational damage. Organizations looking to streamline electronic health records with automation must prioritize audit trails from day one.
You can run a security audit on your n8n instance, to detect common security issues. You can run an audit using the CLI, the public API, or the n8n node. Begin by auditing existing workflows to identify:
Start with identity provider integration. Configure SAML or OIDC with your existing SSO platform (Okta, Azure AD, Google Workspace). Map existing organizational units to n8n projects aligned with business functions or data sensitivity levels.
Implement role assignments:
Audit logs—available in the enterprise edition, tracking who ran what, and when—exist, but native integrations with SIEM platforms (Splunk, Elastic) require custom configuration.
Configure centralized log collection:
Organizations implementing comprehensive monitoring should review how to address AI security and cyber risks with intelligent defense to understand broader security context.
Smaller teams rely on the built-in versioning, but enterprises with stricter controls often extend it with GitOps pipelines. Storing workflows as JSON in a repo makes approvals and rollbacks auditable in the same way as code deployments. That way compliance doesn't depend on a single platform feature.
Implement workflow-as-code practices:
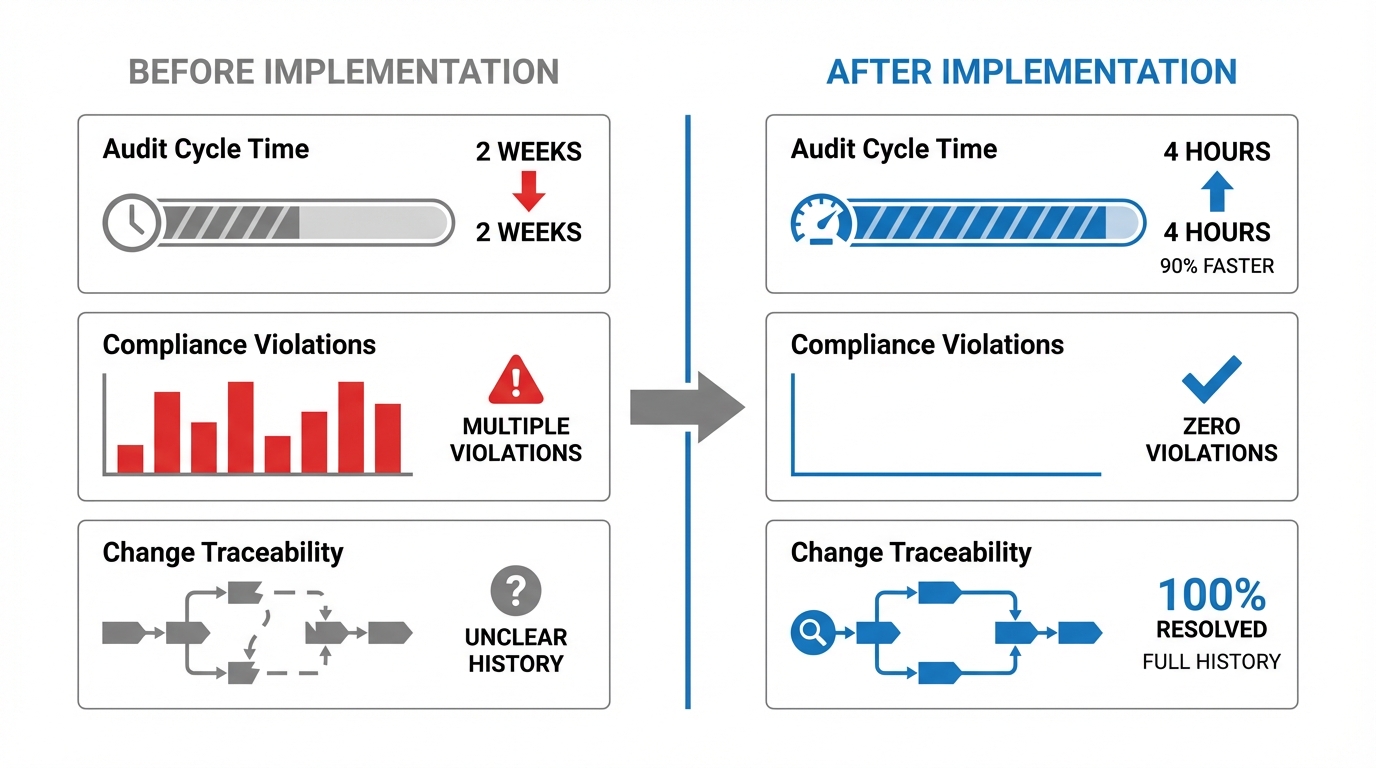
Within six months, the solution delivered measurable outcomes: 90% Faster Audits—automated checks reduced audit cycle time from 2 weeks to 4 hours. Zero Compliance Violations—all workflows passed regulatory reviews post-implementation. Full Change Traceability—Git history resolved 100% of "who changed what" inquiries.
Prepare audit-ready documentation:
The n8n Expert Program 2025 helped a Fortune 500 enterprise client, a global financial services firm, automate and secure their workflow auditing processes. The project leveraged Python scripting, Git version control, and automated compliance logging to create a robust auditing framework, ensuring adherence to regulatory standards like GDPR and SOX.
The implementation addressed critical challenges:
Manual Auditing Overhead
Custom Python scripts parsed n8n workflow JSONs, flagging non-compliant nodes (e.g., unencrypted data transfers), and integrated with the client's SIEM (Security Information and Event Management) system to alert on anomalies.
Scalability Issues
Git repositories version-controlled n8n workflows, with commit hooks enforcing peer reviews. Automated git diff reports highlighted changes, attributing modifications to specific teams/users.
Regulatory Risks
A logging pipeline using Python and PostgreSQL recorded workflow executions, approvals, and errors. Logs were cryptographically signed and stored in a tamper-proof blockchain layer for audits.
Results were dramatic. During a surprise SOX audit, the client generated compliant reports in minutes—previously a 3-day effort. Cost Savings eliminated 3 FTEs previously dedicated to manual audits (~$250K/year). Organizations implementing similar solutions for extracting key insights from financial documents using AI can benefit from the same architectural principles.
While n8n provides the foundation for secure workflow automation, enterprises face months of infrastructure work, security hardening, and compliance configuration. Shakudo eliminates this implementation gap.
Shakudo delivers pre-configured, audit-ready n8n deployments on your private infrastructure with enterprise security controls already integrated. This includes centralized audit logging streaming to your SIEM, RBAC mapped to your organizational structure, encrypted credential management with external vaults, and compliance-ready reporting for SOC 2, ISO 27001, and GDPR frameworks.
Your n8n workflows run entirely within your private cloud or on-premises environment, ensuring complete data sovereignty. Shakudo handles the operational complexity of high availability configurations, automated backup procedures, disaster recovery testing, and security patch management while your teams focus on building automation that drives business value.
Deployment accelerates from months to days. You maintain full workflow ownership and audit control without vendor lock-in while gaining production-ready infrastructure that meets regulatory requirements from day one.
Enterprise auditability transforms workflow automation from a compliance burden into a strategic capability. Organizations with comprehensive audit trails respond to regulatory inquiries in hours instead of weeks, prove data handling practices to security-conscious customers, identify and remediate security incidents before they escalate, and scale automation confidently across regulated business units.
We've seen enterprises standardize on n8n as their automation backbone precisely because it avoids the "black box" limitations of other platforms. The combination of self-hosted control, enterprise-grade security features, and comprehensive audit capabilities makes n8n uniquely suited for regulated industries where automation without governance is unacceptable.
For teams ready to move beyond manual compliance tracking and embrace audit-ready automation, the path forward is clear: implement RBAC aligned with least-privilege principles, stream comprehensive audit logs to centralized monitoring, integrate with enterprise secret managers and identity providers, enforce GitOps workflows with peer review and testing, and document everything for compliance teams.
The question is no longer whether enterprises can automate securely with n8n. The question is how quickly you can implement the governance controls that turn automation from a risk into a competitive advantage.

When a global financial services firm faced growing compliance demands, they needed a scalable, traceable solution to audit their n8n workflows. The problem was universal: 30% of firms have faced fines due to poor record-keeping in the past five years. As 25% of Fortune 500 companies adopt n8n for business-critical workflows, the question shifts from whether to automate to how to automate securely.
Automation without governance creates liability. Enterprises don't reject automation—they reject risk. If your workflows can't prove where data lives, who touched it, and how it's protected, the deal stalls. For regulated industries operating under GDPR, HIPAA, SOC 2, or ISO 27001, comprehensive audit trails transform from nice-to-have features into regulatory requirements.
Traditional workflow automation platforms create a dangerous blind spot. When workflows execute automatically, touching sensitive data across dozens of systems, organizations face three critical gaps:

Lack of Traceability
Without detailed logging, teams cannot answer fundamental questions during audits: Who created this workflow? When was it last modified? Which user triggered this execution? What data did it access?
Insufficient Access Controls
Many organizations discover only after a disruption that their automation estate has grown beyond control: workflows are undocumented, access is unrestricted, and critical processes rely on ad hoc scripts with no rollback or monitoring. This creates compliance violations waiting to happen.
Manual Compliance Burden
Auditing workflows manually was time-consuming, error-prone, and failed to meet real-time compliance demands. Finance teams keep spreadsheets tracking workflow changes. Security teams manually review execution logs. Compliance officers spend weeks preparing audit documentation.
The consequences are measurable. When regulators requested evidence during an annual exam, export time fell from days to minutes at a fintech lender with immutable audit trails, saving six figures in potential fines.
Securing n8n workflows for enterprise auditability requires a layered security architecture that addresses authentication, authorization, logging, and data protection.
RBAC is a way of managing access to workflows and credentials based on user roles and projects. You group workflows into projects, and user access depends on the user's project role. This enables separation of duties required by regulatory frameworks.
n8n provides granular role types:
n8n uses projects to group workflows and credentials, and assigns roles to users in each project. This means that a single user can have different roles in different projects, giving them different levels of access. For example, a data engineer might have Editor permissions in the Marketing Analytics project but only Viewer access to Finance Compliance workflows.
Enterprises rarely want standalone login systems. n8n integrates with identity providers (Okta, Azure AD, etc.), enabling Single Sign-On (SSO) and central policy enforcement. SSO, SAML, and LDAP are available with n8n's Enterprise plan, allowing organizations to enforce password policies, session timeouts, and conditional access rules centrally.
n8n should counter weak authentication by enforcing strong passwords with MFA, integrating with OIDC or SAML for centralized access control, applying least-privilege roles, and configuring sessions and API tokens to be short-lived, rotated often, and scoped minimally. This eliminates the risk of credential stuffing attacks and ensures departed employees lose access immediately when disabled in the central identity provider.
Every workflow edit, execution, and deployment can be logged. This makes compliance audits far easier and gives internal teams confidence that automations can be traced. Authorized users can query the log info as necessary to trace actions to individual users. We keep audit log history and historical activity records for at least 12 months, with at least the last three months immediately available for analysis.
Enterprise audit trails capture:
Write-once storage, cryptographic hashing, and chained log entries ensure that any alteration breaks the chain or hash, flagging tampering attempts. This immutability proves to auditors that logs haven't been retroactively modified to hide security incidents.

The n8n editor should be hidden behind a VPN or allow-listed IPs, with inbound traffic controlled through firewalls or cloud security groups. The admin UI must never be exposed directly to the internet. For high-security environments, consider binding the editor interface to localhost only and exposing it through a bastion host or SSH tunnel.
Production deployments should implement:
Integrate with 3rd-party secret management tools (HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) to securely fetch and inject your encrypted credentials. This prevents storing API keys, database passwords, and service account tokens directly in workflow definitions.
External secret management provides:
Unlike SaaS platforms, n8n can run entirely inside a private cloud or on-premises environment. Sensitive data never leaves your controlled infrastructure—a critical requirement for GDPR, ISO 27001, or SOC 2 compliance.
n8n aligns its security program to SOC 2, a standard framework for security compliance. That means we have implemented processes and follow procedures that uphold high standards of security for our customers' data. We undergo continuous evaluation and annual audits by an independent auditor.
For self-hosted deployments, organizations must implement controls around:
For regulated teams—finance, healthcare, public sector—data location, isolation, and control are non-negotiable. Self-hosting n8n lets you pin data to a specific geography (EU, US, APAC), enforce network boundaries (VPC, private subnets, IP allowlists).
n8n can be configured to support GDPR and similar data protection regulations. Implement data minimization in your workflows, maintain audit logs for data processing activities, and ensure your automation design allows data subject access, correction, or deletion requests.
Patient data must remain fully compliant with HIPAA. Self-hosted n8n provides a clear advantage. Healthcare organizations must implement Business Associate Agreements, encrypt Protected Health Information at rest and in transit, maintain detailed access logs showing who viewed patient data, and implement automatic session timeouts to prevent unauthorized viewing.
Automated alerts on bulk downloads helped detect and stop an insider threat at a hospital chain, avoiding HIPAA breach penalties and reputational damage. Organizations looking to streamline electronic health records with automation must prioritize audit trails from day one.
You can run a security audit on your n8n instance, to detect common security issues. You can run an audit using the CLI, the public API, or the n8n node. Begin by auditing existing workflows to identify:
Start with identity provider integration. Configure SAML or OIDC with your existing SSO platform (Okta, Azure AD, Google Workspace). Map existing organizational units to n8n projects aligned with business functions or data sensitivity levels.
Implement role assignments:
Audit logs—available in the enterprise edition, tracking who ran what, and when—exist, but native integrations with SIEM platforms (Splunk, Elastic) require custom configuration.
Configure centralized log collection:
Organizations implementing comprehensive monitoring should review how to address AI security and cyber risks with intelligent defense to understand broader security context.
Smaller teams rely on the built-in versioning, but enterprises with stricter controls often extend it with GitOps pipelines. Storing workflows as JSON in a repo makes approvals and rollbacks auditable in the same way as code deployments. That way compliance doesn't depend on a single platform feature.
Implement workflow-as-code practices:
Within six months, the solution delivered measurable outcomes: 90% Faster Audits—automated checks reduced audit cycle time from 2 weeks to 4 hours. Zero Compliance Violations—all workflows passed regulatory reviews post-implementation. Full Change Traceability—Git history resolved 100% of "who changed what" inquiries.

Prepare audit-ready documentation:
The n8n Expert Program 2025 helped a Fortune 500 enterprise client, a global financial services firm, automate and secure their workflow auditing processes. The project leveraged Python scripting, Git version control, and automated compliance logging to create a robust auditing framework, ensuring adherence to regulatory standards like GDPR and SOX.
The implementation addressed critical challenges:
Manual Auditing Overhead
Custom Python scripts parsed n8n workflow JSONs, flagging non-compliant nodes (e.g., unencrypted data transfers), and integrated with the client's SIEM (Security Information and Event Management) system to alert on anomalies.
Scalability Issues
Git repositories version-controlled n8n workflows, with commit hooks enforcing peer reviews. Automated git diff reports highlighted changes, attributing modifications to specific teams/users.
Regulatory Risks
A logging pipeline using Python and PostgreSQL recorded workflow executions, approvals, and errors. Logs were cryptographically signed and stored in a tamper-proof blockchain layer for audits.
Results were dramatic. During a surprise SOX audit, the client generated compliant reports in minutes—previously a 3-day effort. Cost Savings eliminated 3 FTEs previously dedicated to manual audits (~$250K/year). Organizations implementing similar solutions for extracting key insights from financial documents using AI can benefit from the same architectural principles.
While n8n provides the foundation for secure workflow automation, enterprises face months of infrastructure work, security hardening, and compliance configuration. Shakudo eliminates this implementation gap.
Shakudo delivers pre-configured, audit-ready n8n deployments on your private infrastructure with enterprise security controls already integrated. This includes centralized audit logging streaming to your SIEM, RBAC mapped to your organizational structure, encrypted credential management with external vaults, and compliance-ready reporting for SOC 2, ISO 27001, and GDPR frameworks.
Your n8n workflows run entirely within your private cloud or on-premises environment, ensuring complete data sovereignty. Shakudo handles the operational complexity of high availability configurations, automated backup procedures, disaster recovery testing, and security patch management while your teams focus on building automation that drives business value.
Deployment accelerates from months to days. You maintain full workflow ownership and audit control without vendor lock-in while gaining production-ready infrastructure that meets regulatory requirements from day one.
Enterprise auditability transforms workflow automation from a compliance burden into a strategic capability. Organizations with comprehensive audit trails respond to regulatory inquiries in hours instead of weeks, prove data handling practices to security-conscious customers, identify and remediate security incidents before they escalate, and scale automation confidently across regulated business units.
We've seen enterprises standardize on n8n as their automation backbone precisely because it avoids the "black box" limitations of other platforms. The combination of self-hosted control, enterprise-grade security features, and comprehensive audit capabilities makes n8n uniquely suited for regulated industries where automation without governance is unacceptable.
For teams ready to move beyond manual compliance tracking and embrace audit-ready automation, the path forward is clear: implement RBAC aligned with least-privilege principles, stream comprehensive audit logs to centralized monitoring, integrate with enterprise secret managers and identity providers, enforce GitOps workflows with peer review and testing, and document everything for compliance teams.
The question is no longer whether enterprises can automate securely with n8n. The question is how quickly you can implement the governance controls that turn automation from a risk into a competitive advantage.
When a global financial services firm faced growing compliance demands, they needed a scalable, traceable solution to audit their n8n workflows. The problem was universal: 30% of firms have faced fines due to poor record-keeping in the past five years. As 25% of Fortune 500 companies adopt n8n for business-critical workflows, the question shifts from whether to automate to how to automate securely.
Automation without governance creates liability. Enterprises don't reject automation—they reject risk. If your workflows can't prove where data lives, who touched it, and how it's protected, the deal stalls. For regulated industries operating under GDPR, HIPAA, SOC 2, or ISO 27001, comprehensive audit trails transform from nice-to-have features into regulatory requirements.
Traditional workflow automation platforms create a dangerous blind spot. When workflows execute automatically, touching sensitive data across dozens of systems, organizations face three critical gaps:

Lack of Traceability
Without detailed logging, teams cannot answer fundamental questions during audits: Who created this workflow? When was it last modified? Which user triggered this execution? What data did it access?
Insufficient Access Controls
Many organizations discover only after a disruption that their automation estate has grown beyond control: workflows are undocumented, access is unrestricted, and critical processes rely on ad hoc scripts with no rollback or monitoring. This creates compliance violations waiting to happen.
Manual Compliance Burden
Auditing workflows manually was time-consuming, error-prone, and failed to meet real-time compliance demands. Finance teams keep spreadsheets tracking workflow changes. Security teams manually review execution logs. Compliance officers spend weeks preparing audit documentation.
The consequences are measurable. When regulators requested evidence during an annual exam, export time fell from days to minutes at a fintech lender with immutable audit trails, saving six figures in potential fines.
Securing n8n workflows for enterprise auditability requires a layered security architecture that addresses authentication, authorization, logging, and data protection.
RBAC is a way of managing access to workflows and credentials based on user roles and projects. You group workflows into projects, and user access depends on the user's project role. This enables separation of duties required by regulatory frameworks.
n8n provides granular role types:
n8n uses projects to group workflows and credentials, and assigns roles to users in each project. This means that a single user can have different roles in different projects, giving them different levels of access. For example, a data engineer might have Editor permissions in the Marketing Analytics project but only Viewer access to Finance Compliance workflows.
Enterprises rarely want standalone login systems. n8n integrates with identity providers (Okta, Azure AD, etc.), enabling Single Sign-On (SSO) and central policy enforcement. SSO, SAML, and LDAP are available with n8n's Enterprise plan, allowing organizations to enforce password policies, session timeouts, and conditional access rules centrally.
n8n should counter weak authentication by enforcing strong passwords with MFA, integrating with OIDC or SAML for centralized access control, applying least-privilege roles, and configuring sessions and API tokens to be short-lived, rotated often, and scoped minimally. This eliminates the risk of credential stuffing attacks and ensures departed employees lose access immediately when disabled in the central identity provider.
Every workflow edit, execution, and deployment can be logged. This makes compliance audits far easier and gives internal teams confidence that automations can be traced. Authorized users can query the log info as necessary to trace actions to individual users. We keep audit log history and historical activity records for at least 12 months, with at least the last three months immediately available for analysis.
Enterprise audit trails capture:
Write-once storage, cryptographic hashing, and chained log entries ensure that any alteration breaks the chain or hash, flagging tampering attempts. This immutability proves to auditors that logs haven't been retroactively modified to hide security incidents.

The n8n editor should be hidden behind a VPN or allow-listed IPs, with inbound traffic controlled through firewalls or cloud security groups. The admin UI must never be exposed directly to the internet. For high-security environments, consider binding the editor interface to localhost only and exposing it through a bastion host or SSH tunnel.
Production deployments should implement:
Integrate with 3rd-party secret management tools (HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) to securely fetch and inject your encrypted credentials. This prevents storing API keys, database passwords, and service account tokens directly in workflow definitions.
External secret management provides:
Unlike SaaS platforms, n8n can run entirely inside a private cloud or on-premises environment. Sensitive data never leaves your controlled infrastructure—a critical requirement for GDPR, ISO 27001, or SOC 2 compliance.
n8n aligns its security program to SOC 2, a standard framework for security compliance. That means we have implemented processes and follow procedures that uphold high standards of security for our customers' data. We undergo continuous evaluation and annual audits by an independent auditor.
For self-hosted deployments, organizations must implement controls around:
For regulated teams—finance, healthcare, public sector—data location, isolation, and control are non-negotiable. Self-hosting n8n lets you pin data to a specific geography (EU, US, APAC), enforce network boundaries (VPC, private subnets, IP allowlists).
n8n can be configured to support GDPR and similar data protection regulations. Implement data minimization in your workflows, maintain audit logs for data processing activities, and ensure your automation design allows data subject access, correction, or deletion requests.
Patient data must remain fully compliant with HIPAA. Self-hosted n8n provides a clear advantage. Healthcare organizations must implement Business Associate Agreements, encrypt Protected Health Information at rest and in transit, maintain detailed access logs showing who viewed patient data, and implement automatic session timeouts to prevent unauthorized viewing.
Automated alerts on bulk downloads helped detect and stop an insider threat at a hospital chain, avoiding HIPAA breach penalties and reputational damage. Organizations looking to streamline electronic health records with automation must prioritize audit trails from day one.
You can run a security audit on your n8n instance, to detect common security issues. You can run an audit using the CLI, the public API, or the n8n node. Begin by auditing existing workflows to identify:
Start with identity provider integration. Configure SAML or OIDC with your existing SSO platform (Okta, Azure AD, Google Workspace). Map existing organizational units to n8n projects aligned with business functions or data sensitivity levels.
Implement role assignments:
Audit logs—available in the enterprise edition, tracking who ran what, and when—exist, but native integrations with SIEM platforms (Splunk, Elastic) require custom configuration.
Configure centralized log collection:
Organizations implementing comprehensive monitoring should review how to address AI security and cyber risks with intelligent defense to understand broader security context.
Smaller teams rely on the built-in versioning, but enterprises with stricter controls often extend it with GitOps pipelines. Storing workflows as JSON in a repo makes approvals and rollbacks auditable in the same way as code deployments. That way compliance doesn't depend on a single platform feature.
Implement workflow-as-code practices:
Within six months, the solution delivered measurable outcomes: 90% Faster Audits—automated checks reduced audit cycle time from 2 weeks to 4 hours. Zero Compliance Violations—all workflows passed regulatory reviews post-implementation. Full Change Traceability—Git history resolved 100% of "who changed what" inquiries.

Prepare audit-ready documentation:
The n8n Expert Program 2025 helped a Fortune 500 enterprise client, a global financial services firm, automate and secure their workflow auditing processes. The project leveraged Python scripting, Git version control, and automated compliance logging to create a robust auditing framework, ensuring adherence to regulatory standards like GDPR and SOX.
The implementation addressed critical challenges:
Manual Auditing Overhead
Custom Python scripts parsed n8n workflow JSONs, flagging non-compliant nodes (e.g., unencrypted data transfers), and integrated with the client's SIEM (Security Information and Event Management) system to alert on anomalies.
Scalability Issues
Git repositories version-controlled n8n workflows, with commit hooks enforcing peer reviews. Automated git diff reports highlighted changes, attributing modifications to specific teams/users.
Regulatory Risks
A logging pipeline using Python and PostgreSQL recorded workflow executions, approvals, and errors. Logs were cryptographically signed and stored in a tamper-proof blockchain layer for audits.
Results were dramatic. During a surprise SOX audit, the client generated compliant reports in minutes—previously a 3-day effort. Cost Savings eliminated 3 FTEs previously dedicated to manual audits (~$250K/year). Organizations implementing similar solutions for extracting key insights from financial documents using AI can benefit from the same architectural principles.
While n8n provides the foundation for secure workflow automation, enterprises face months of infrastructure work, security hardening, and compliance configuration. Shakudo eliminates this implementation gap.
Shakudo delivers pre-configured, audit-ready n8n deployments on your private infrastructure with enterprise security controls already integrated. This includes centralized audit logging streaming to your SIEM, RBAC mapped to your organizational structure, encrypted credential management with external vaults, and compliance-ready reporting for SOC 2, ISO 27001, and GDPR frameworks.
Your n8n workflows run entirely within your private cloud or on-premises environment, ensuring complete data sovereignty. Shakudo handles the operational complexity of high availability configurations, automated backup procedures, disaster recovery testing, and security patch management while your teams focus on building automation that drives business value.
Deployment accelerates from months to days. You maintain full workflow ownership and audit control without vendor lock-in while gaining production-ready infrastructure that meets regulatory requirements from day one.
Enterprise auditability transforms workflow automation from a compliance burden into a strategic capability. Organizations with comprehensive audit trails respond to regulatory inquiries in hours instead of weeks, prove data handling practices to security-conscious customers, identify and remediate security incidents before they escalate, and scale automation confidently across regulated business units.
We've seen enterprises standardize on n8n as their automation backbone precisely because it avoids the "black box" limitations of other platforms. The combination of self-hosted control, enterprise-grade security features, and comprehensive audit capabilities makes n8n uniquely suited for regulated industries where automation without governance is unacceptable.
For teams ready to move beyond manual compliance tracking and embrace audit-ready automation, the path forward is clear: implement RBAC aligned with least-privilege principles, stream comprehensive audit logs to centralized monitoring, integrate with enterprise secret managers and identity providers, enforce GitOps workflows with peer review and testing, and document everything for compliance teams.
The question is no longer whether enterprises can automate securely with n8n. The question is how quickly you can implement the governance controls that turn automation from a risk into a competitive advantage.